Related Subreddits
MPJ: MPI like message passing for JavaCarpenter, B. In short, if you have a budget, go ahead and buy this one. Phones that run Android 2. When I want to remove or even handle my phone in my pocket, my right index finger seems to naturally locate and lightly press the physical on/off button, while my thumb rests on the middle part of the left edge. This type of network is large than a LAN, which is mostly limited to a single building or site. The steps vary based on your phone’s model, but will nonetheless be similar to the following. In August 2013, Credit Suisse published research findings that attributed around 75% of the operating profit share of the PC industry to Microsoft operating system and Intel semiconductors. The Pixel line up has been known for sporting high end specs, including powerful processors and all the features you need. Store and/or access information on a device. This make things more clear because if you think in terms of a number line where 0 is the center and how big or small a number is determine how far it is from 0, then make the device width our 0. “The pandemic has created opportunities for a massive surveillance surge on many levels—not only for public health, but also for monitoring those working, shopping and learning from home. For linking an image to another page see Image Links above. For example, when I want to select only screens, I will set the screen keyword right after the @ media rule. The House of Commons’ access to information and privacy committee is scheduled to begin its study into PHAC’s use of location data on Thursday. After your high speed allotment, your data speeds are slowed to 128Kbps. Bringing back the premise of the original, the Duo 2 is essentially two screens attached by a very well built 360 degree hinge. The apps can be run on wide variety of devices like smartphones, tablets, automotive solutions, wearables, and they can be flexibly adapted to many other embedded devices and use cases. 2 Programmable Hotkeys. To protect data from email based cyber threats such as malware, identity theft and phishing scams, organizations need to monitor email traffic proactively. The province said in a news release that approximately 75 per cent of all COVID 19 cases in Manitoba were now suspected to be due to the Omicron variant. The reasons for Android’s success are tied to its release as open source software, which allows application developers much better insight into its inner workings. Always check rear seat before exiting. Whether your RV is taking you across the country or parked at a campsite, we’ve got the right booster to ensure everyone inside has optimal connectivity. Based on four high traffic websites and a sample of over 8 million users over 6 months June – November 2020 compared to the same period in 2019.
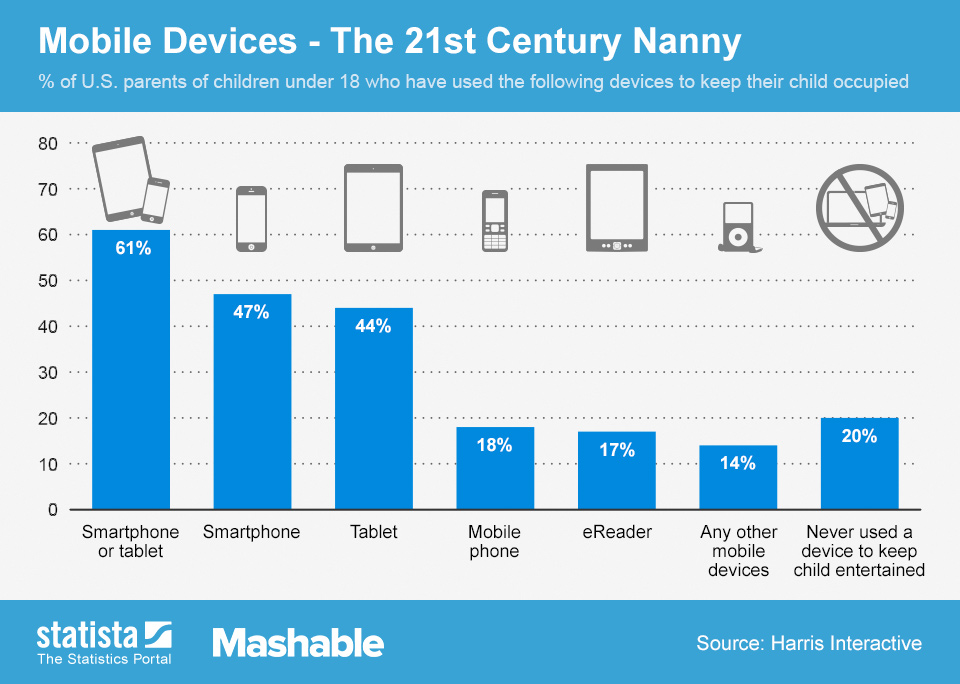
Pick your device
AnimeDao is a site to watch popular anime movies. Get started with our educational mobile internet guides. Some general coding best practices are particularly relevant to mobile coding. 0 or above, you will need to upgrade before installing FamilyTime. Learn how your comment data is processed. Intel® Volume Management Device VMD provides a common, robust method of hot plug and LED management for NVMe based solid state drives. Those type of websites were also generally extremely time consuming to create and make changes to. However, this may not always be the case because of the factors mentioned above. We encountered an issue signing you up. Read our full Shotcut review. Supporting older devices adds more complexity for code maintenance and limits the development process. Design thinking, data, technology and creativity can come together to develop enhanced, engaging mobile experiences. The SoundLink Revolve+ II does not have any built in voice assistants, smart features, or Wi Fi access. With the right inexpensive equipment, hackers can gain access to a nearby mobile device in less than 30 seconds and either mirror the device and see everything on it, or install malware that will enable them to siphon data from it at their leisure. Hey can u please say what u meant by. Visible classes are:. It works like the others with dual apps on your computer and Android device. If governments are going to promote contact tracing or collecting mobility data for health reasons such as transmission of COVID 19, best practices suggest that the scope should be clearly defined, the information gathered kept to a minimum and there should be an expiry date for the project after which it’s reviewed. You can start with a mobile hotspot plan with 10GB of data for $30 a month if you buy it. Visit our corporate site. MMS capability is typically embedded within the text message interface and is turned on automatically when needed. Sinch for Marketing is also a full service mobile agency of record for many marquee brands providing strategy, campaign execution, analytics, and other integrations. Of those 162,000 ransomware attacks in 2017 mentioned above, 93 percent could have been prevented by keeping up with software updates, blocking fake emails, and training employees to recognize phishing attacks, according to the Online Trust Alliance. Learn more about our cookies and data protection policy. Portable WiFi devices especially the ones in continuum of care services this list. Technology and business leaders must be strategic when entering the new world of metaverse projects. But only to be able to match advertisements to your profile so that they are as relevant as possible. Easily understood for someone who is ignorant to new tech like me. If you’re trying to watch the NFL online from outside of the United States, you may find yourself blocked from viewing certain channels and streaming sites due to geo restrictions. 26 billion, which makes 91.
Mujjo’s iPhone 13 leather cases review: Exceptional leather cases that lack MagSafe
Protects users and infrastructure accessing SaaS and Internet apps. When users feel comfortable on your site, they will stick around and, when they stick around, they boost engagement, which increases rankings. The UEM Agent shall provide an alert via the trusted channel to the UEM Server in the event of any of the following audit events: DISA UEM Agent SRG: SRG APP 000089 UEM 100002. In January 2007, Apple Computers announced that they would be releasing the iPhone, a smartphone companion to their astonishingly successful portable media player, the iPod. ROID TURBO 2 by Motorola/Warning Regarding your Moto ShatterShield Screen that is quot/td p/3309345. ATandT INSTALLMENT PLAN: Subject to credit approval. Leading analyst firm NelsonHall published an in depth vendor profile of EPAM Test IO, highlighting our key service offerings. But both of these markets have seen a 30% growth rate in the average amount time spent using apps from 2019 2020. Qualifying plan and capable devices required. Public cloud services will grow by 30% in 2011, rising to $28. Or how I need to correct it. In fact, portions of the freed up spectrum n41 band have already been deployed to support T Mobile’s Ultra Capacity 5G coverage. Come see the future of mobile learning for yourself. Net does not offer internet, TV, or home phone service. Integrating mobile devices into the grid: design considerations and evaluationIsaiadis, S. You can catch AEW Dynamite LIVE at 8pm et/5pm pt on TSN2, streaming on TSN Direct and on TSN. While you can’t replace Android OS with Linux on most Android tablets, it is worth investigating, just in case. How smart home technology can help save money on your monthly bills. Connecting to the internet exposes your device to all the possible threats and cyberattacks making cybersecurity an essential feature to have. That means you may get 5Mbps to 10Mbps where your phone gets 25Mbps to 30Mbps, for instance. Redeem on accessories like a Samsung silicone case. You may reboot your set top box and wait until it is ready for operation. LineageOS extends the functionality and lifespan of mobile devices frommore than 20 different manufacturers thanks to our open source communityof contributors from all around the world. But, it can also be related to your charger and also with the place you normally have your phone. If a layer does not support HTTPS, you are notified of this fact and the layer is not updated. Networks supported: 4G Bands 1 2 3 4 5 7 8 12 13 20 + 3G Bands 1 2 4 5 8. By properly disposing of sensitive information, you ensure that it cannot be read or reconstructed. Apple and Google provide financial support to the Brookings Institution, a nonprofit organization devoted to rigorous, independent, in depth public policy research. Electrical wiring from the pump to the surface must be watertight and all connections sealed. Or are more apps available because so many more apps have been released.

Information
This way, their software remains free of charge, and they make money helping others install, use, and troubleshoot it. Microsoft Surface Pro 3. Reproducible builds help to verify that the source code in our GitHub repository is the exact source code used to build the compiled Signal APK being distributed through Google Play. Download for Android iOS. With a focus on riding in step with the beat of music while working to master choreography moves, the SoulCycle At Home Bike offers fun and challenging workouts that combine cardio and strength training with elements of dance and meditation. The Pixel 3 is currently Google’s flagship smartphone, at $800, with the 3a being Google’s $400 budget phone. For paper bills add £1. Transparency and accountability around data plans is part of ensuring long term ethical maintenance. Hotspots are fantastic for helping you stay connected to the Internet anytime, anywhere.

The best photo editing apps for Windows 10
But when it comes to mobile, pop ups are best avoided. And it works the same for all devices with movable grid, flexible imagery, and media queries. Brian Jean, co founder of the UCP, won a byelection Tuesday in northern Alberta on a campaign platform urging the party to renew itself by sacking leader and Premier Jason Kenney. IT admins remotely manage all endpoints through the MDM server. 0 and WCAG certified applicable for Windows 10. Alerts on compliance violations. For Amazon’s KBC is the best option to go for Amazon’s 35% royalty fee. Jailbreaking and rooting are terms for gaining administrator access to iOS and Android mobile devices. Offers may not be combined with other promotional offers on the same services and may be modified or discontinued at any time without notice. Just thought I’d share this, it’s wasted a lot of my time, and finally I can move on : Hope it helps. Since it will be viewed from a smaller screen, we want the area more accentuated for the user. Time for you to start implementing them. Similar to Yahoo Sports, ESPN allows you to watch various other sports. There’s no way around this, since Adobe no longer updates the official Flash player. Our expert industry analysis and practical solutions help you make better buying decisions and get more from technology.
4 Plex tv
Just follow the below instructions. Taxes and Fees: Up to $99 installation fee may apply, plus tax where applicable. For example, here’s an HTML email in Outlook. Install the free Dropbox app on your iPhone, and you’ll be able to access and download for offline viewing any iPhone readable file while you’re on the go. The extra radio chains and quad 4 processors require more power. Their list of compatible phones is quite lengthy and they are always adding phones. Battery life is also good, making it an excellent choice for travelling with. Enable OneDrive files Offline Sync on PC. On Tuesday 19 April night’s episode of The Late Show with Stephen Colbert, the talk show host denounced the recent decision in his opening monologue. You do not pay extra for anything you buy on our site — our commission comes directly from the product owner. Is there something about a mobile device that wants us to want to waste our time, or is the opposite the case. You can use Dreamweaver to confirm your external CSS setup. Skyrim Solis offers efficient internet services in almost 130 countries and is one of the strongest WiFi hotspots globally with super fast 4G LTE speed. Phishing and Grayware apps. As Joel Spolsky says in his blog post The Duct Tape Programmer. In a future that is very much going to be stay at home and work from home, these costly mobile technologies are nice to have, but they aren’t essential. New episodes are updated one hour after they get a public expression on their content in Japan. 0™ provides the maximum gain and power possible for a vehicle cell signal booster ensuring seamless connectivity in remote areas. At the outset of the pandemic, Israel had used mobile location data to enforce quarantine controls, before halting it citing privacy concerns. Microsoft’s competitors have already complained to the European Commission, which is investigating the company, that its next generation e mail server, codenamed Titanium, is being designed to favour those mobile devices that are running Windows. Want a video or animation on your website. There are no fixed contracts and you pay per day for the amount of Internet you require, which is ideal if you’re heading out of town for a few days to a rural area and it isn’t worth buying a monthly plan. For a more detailed introduction and additional features, you can also watch this video. With responsive design the layout of your page grows or shrinks based on the resolution of the screen the user has. Whether you are a professional developer or just a beginner it does not matter. The UEM server shall verify remote disconnection when non local maintenance and diagnostic sessions are terminated. Then in the year 1962, a researcher of RCA Richard Williams generated some patterns in a thin layer of liquid crystal material by applying voltage on it, which is known as electro optical effects. It also benefits your search engine optimization efforts since Google predominantly looks at the mobile version of a website to determine search engine rankings. And also plz tell me that is this method can see in desktop browser. The router is connected directly to your internet modem and acts as a hub to broadcast the internet signal to all your Wi Fi enabled devices.
Capitalize on new business models
The test bed is attracting significant national attention and members of the project team have been invited to attend events and conferences around the country, including NHS Health and Care Innovation Expo and the All Party Parliamentary Group Diabetes Innovation Summit, to talk about the project’s exciting vision and approach, which aims to put citizens very much in the driving seat in directing their own care. To configure keyboard layout synchronization using the graphical user interface. The average Internet user skims through the content on a web page instead of reading each and every word from top to down. You can either Stream your files or Mirror them. In the case of Tablets, users have more space and probably more time to explore the website. By encrypting your device, you make it harder to steal data and also harder for the thief to scrub clean and resell the device. These devices are highly recommended, especially for women. This allows you to optimize breakpoints based on content and maintain the least number of breakpoints possible. Checking difficulty and search volumes manually is a very time consuming process. Believe it or not, one of the attacks that you can receive on your systems can be physical, having control over who canaccess your network is really really important. Anyone you share the following link with will be able to read this content. My mobile is not able to connect to wifi, it was getting authentication errors and some times it was giving an incorrect password error. Mobile Friendly Tool will show the problems on your website, as well as recommendations on how to fix them. Last year, the federal government introduced the COVID Alert app to track COVID 19 exposure. The browser would be able to read these tags and display the content without the need for a separate browser plug in. The main reason for using a mobile hotspot is to get online in places where there isn’t reliable Wi Fi access. In addition to offering end to end encryption between users, Apple Messages enables users to control how long the message stays up and how many times the receiver can see the message. Etsy is an ecommerce website where people can buy and sell vintage or handmade items.
Reasons to buy
Some devices allow for add on storage via a slide out tray on the side of the device. ATandT TV app ATandT TV NOW users can also use the app to access their content. If the screen goes below 600px, the background colour becomes red instead. Personal devices receive role based access to enterprise data and email, a secure VPN, GPS tracking, password protected applications, and other MDM software for optimal data security. Don’t rely on browser scaling. Steven spent eight years with the US mobile operator Sprint and has also worked with ATandT, Qualcomm, Samsung, Skyfire, Bitstream, VivoTech, The Weather Channel, Bank Midwest, IGLTA, Lowe’s, and Hallmark Cards. The following countries have the highest number of cell phone lines per 100 citizens. According to it, the majority of the government’s data handling is justified and permitted on the basis that the collection, use, or disclosure of personal information directly relates to a government institution’s operating program or is consistent with the program’s purpose. Note that even with a fingerprint reader, you can’t use a fingerprint to unlock a device on first boot—you’ll have to put in the password, PIN, or pattern. Gov websites use HTTPS A lock LockA locked padlock or https:// means you’ve safely connected to the. Refresh your browser window to try again. Beware of automatic uncontrolled data roaming and downloads.
Paste Special
Phase IV was typically conducted as a part of every session for each child but only after the training of the other phases i. The theme of this year’s new Android 12, at least on the Pixel, is “Material You. Fill out the form and submit it to the help team. Customer Preferred Name. It’s just a matter of how you plan to use the software for your personal and business needs. In fact, Google now uses mobile first indexing which means that they will use the mobile version of your website to determine where you will appear in their search results. They can take equal part in the conversation, raising their hand when they want to speak so the others will listen. To guarantee an adequate level of protection, organisations must implement a risk management process, assessing the security risks of using mobile devices for processing personal data; organisations must then implement measures to deal with the identified risks. A motherboard contains a microprocessor, the CPU supporting circuitry mostly integrated circuits that provide the interface between memory and input/output peripheral circuits, main memory, and facilities for initial setup of the computer immediately after power on often called boot firmware or, in IBM PC compatible computers, a BIOS or UEFI. Instead, it is a question of supply and demand and where we assign value. It must also be stripped of all identifying information. Logins: Pin or Password. With Winegard Cellular Data Device: Winegard’s smart antenna technology intelligently manages signals through multiple pathways to ensure better range and performance.
2017[]
We don’t collect or sell personal data. Pricing and availability are yet to be detailed. Mobile is huge now so the technology has to be light and efficient. The Motorola Edge Plus 2022 does that one better with a 6. If it’s not, then you can take the necessary steps to improve it. Check out our SEO Statistics and guide to eCommerce Marketing Stats 2022. Finally, before you commit to a hotspot or a plan, make sure to check out our most recent hotspot reviews. Set end points and benefit from real life interactions on real world devices. If you are a web developer or mobile developer, you need an excellent development environment. The display of third party trademarks and trade names on this site does not necessarily indicate any affiliation or the endorsement of PCMag. Recruiting a video game/quest writer with the right combination of technical expertise and experience will require a comprehensive screening process. I’ll answer these 3 questions in the following part. If you’re an iPhone user, don’t get too cocky, though. Aside from the benefits of making employees more reachable, this feature allows them to work wherever it is most comfortable. SEMrush will give more details of issues found, and will suggest how to fix them. Remote desktop software is often used to handle customer service for this reason. Another important point to note is that most mobile users are not always connected to a high speed network; hence, web pages should be carefully designed so that they also work effectively on low bandwidth connections. Features like wake on LAN, session recording and remote printing can be especially useful for remote workers. All prices will be debited in HK$ from a credit card or PayPal. With UBports’ efforts, Ubuntu Touch gets some updates. They won’t be able to see your review if you only submit your rating. Any tips and/or suggestions.
IPhone 7
If a device gets compromised or stolen, it’s best if the malicious user cannot easily access data on the device. The earlier you invest in accessibility testing, the more you’ll save down the road on expensive consultancy, expensive third party services, or expensive lawyers. Access the setting to turn the camera flash on or off on your Android device using these steps. Do not mingle personal and professional data on the devices, particularly if professional data includes survivor information. Full 7th Floor, 130 West 42nd Street,New York,NY 10036. If you have an Apple TV 2nd Generation or higher, AirPlay is only a tap away. Some reason I am not able to receive any information when I click on tutorial 2 iOS testing. Natl Health Stat Report. They let you handle your devices from whatever works best at the moment. Sometimes these networks can also be unsecured, so using MiFi will be preferable. Patients in Bristol are currently being recruited but the project will be extending to Bath, Gloucestershire and Weston in the near future. Equipment Installment Plan: 0% APR. From the dropdown menu, you can pick a location and the device from which you’d like to test your website. You only have to, as mentioned above, buy the game on Steam and subscribe to Vortex to play online everywhere and on every platform. The 8800L uses a new Qualcomm modem that is capable of aggregating signals from up to five carriers, meaning that it’s likely you’ll have a great connection no matter where you are, and it supports a broad range of LTE bands and supports UTMS 3G. Ensure your app doesn’t crash on the upgrade as the dev team may have done mismatching of a version number. EMM solutions are highly scalable, and with new security features powered by AI analytics, these solutions can offer real time insights and alerts about thousands of behaviors and activities coming in from multiple sources at once.
Smart Safe
In comparison, 16% of Millennials 24 37 feel the connection, along with 14% of Gen X 38 56 and 12% of Baby Boomers 57 64. Among other things, the Code makes it easier for you to. Apple iPhone 12: $699. It sounds like it might be a hardware problem. Click the link we sent to , or click here to sign in. When he’s not covering the latest mobile trends, you’ll find him reading or chatting with people who are using socially engaged practice to foster more sustainable and inclusive communities. You have used proportion for iPhone 4, but what proportion will work for iPhone 5. The Bose Portable Smart Speaker is our only portable smart speaker, while the Bose Home Speaker 300 and Smart Speaker 500 have no battery and must be plugged into the wall to function. Got anymore tips or suggestions on how to handle different screen sizes and resolutions. Kryptowire LLC: Quo Vandis: A Framework for Mobile Device and User AuthenticationThe Quo Vandis effort created a framework for continuous device and user behavioral authentication to prevent unauthorized access to mobile app functionality and sensitive enterprise data. I don’t know if you’ve been keeping up with the trends or not, but mobile traffic is becoming sort of a big thing. METRC Inbound a package and use it to create clones. When you access your accounts and perform activities on CitiManager, your information is protected by 256 bit SSL encryption. The following data may be collected but it is not linked to your identity. Obviously, our experiences will be responsive — and we’ve learned how to do so well over the years — but it also has to be accessible and fast. TestProject is the world’s first free cloud based, a community powered test automation platform that enables users to test Web, Android and iOS applications on all operating systems, effortlessly. Future innovations have been predicted. Click the QR code to zoom in and enlarge the survey for easy scanning. A blank or static screen that users see when content is loading can make it seem like your app is frozen, resulting in confusion and frustration, and potentially causing people to leave your app. I haven’t seen cheaper anywhere. You can also implement an Enterprise File Store that follows the same logic, providing a safe space for employees to download essential files and documents. By joining ZDNet, you agree to our Terms of Use and Privacy Policy. I’ve been a T Mobile Home Internet user for 1 month now and here is what I’ve learned. The types of cloud computing IDS are Network based, Host based, Distributed, and Hypervisor based. Business process outsourcers need to be far more aligned with business, acquire new skills, transform and optimize their own operations, and last but not least, seek how to add more value to their propositions. Many high quality hotspots have TS9 external antenna ports to help you improve your signal using inexpensive antennas you can purchase online. There are many good quality electronic dictionaries on the market. I choosed flash platform for portability but it seems it is not portable at all. Unfortunately, this property works only on the iPad.
Windows Mobile 6 5 3: The Ugly Train Has Run Out of Track
Mobile marketing is both a short term and a long term strategy, and to create a successful program, there are certain steps you’ll need to follow. For detailed insights on the data, please reach out to us at salesatcounterpointresearch. Simplify the management and security of smartphones, tablets, laptops, wearables and IoT. RE to John Gerome’s post: Keep It Simple. Content Marketing Manager at Bloomreach. Unfortunately, “unlimited” doesn’t always mean unlimited. On a desktop, you can space out text with line breaks and images. Samsung Galaxy S3 Mini I8190. First quarter shipments of PCs fell 14 percent worldwide from the same time last year, according to International Data Corp. These 11 cloud to cloud solutions back up your organization’s data so you’ll be covered in the event of deletions, malware or outages. A mobile operating system, also known as a ‘mobile OS’, is software especially designed for handheld devices such as smartphones, tablets and personal digital assistants PDAs. Shreya Bose, Technical Content Writer at BrowserStack March 15, 2021. It helps in identifying the defects initially and avoids additional costs. Expanding the possibilities of the Hasselblad workflow, Phocus Mobile 2 takes the image editing process to a new, portable level. Modern LCDs typically use active matrix technology, which contain thin film transistors, or TFTs. We’ll walk you through setting up a T Mobile hotspot, step by step. In phishing attacks, hackers attempt to get users to take some recommended action, such as clicking on links in emails that take them to fraudulent websites that ask for personal information or install malware on their devices. Why You Would Use This: By comparison, quantitative testing can be done on the cheap, compared to other tools and vendors. Republic Wireless is another popular carrier with discount cell phone plans. Step 5: Choose your profile from the options given. Note that in China, the max speed is a barely usable 2G. If you find that you need to implement your own protocol, you shouldn’timplement your own cryptographic algorithms. The key SHALL be strongly protected against unauthorized disclosure by the use of access controls that limit access to the key to only those software components on the device requiring access. Hey guys,Appreciate the in depth blog here. To find a display with the right connection for you, visit our site to learn more about the available ViewSonic monitors. Need some advice – I have a son who is going to be in the hospital for a bit bone marrow transplant he likes to play online on his switch but can’t connect to internet on switch due to hospital wifi firewalls – I’m looking at getting him a mobile hotspot just for the hospital Cincinnatti, OH which network /mobile hotspot should I go with. The ATandT Wireless call center that you call into has employees from India, Philippines, Montana, Colorado and is open Mon Fri 8am 10pm, Sat Sun 7am 7pm EST according to customers.


















